SAML Settings
This page shows the settings for SAML authentication and provisioning as it was configured for your organization.
Note — If you would like to set up SAML authentication, read the procedures for doing so with Microsoft’s Azure Active Directory or Google Cloud’s Identity Platform; these can serve as examples for setting up authentication with another identity provider using the required attributes listed on this page.
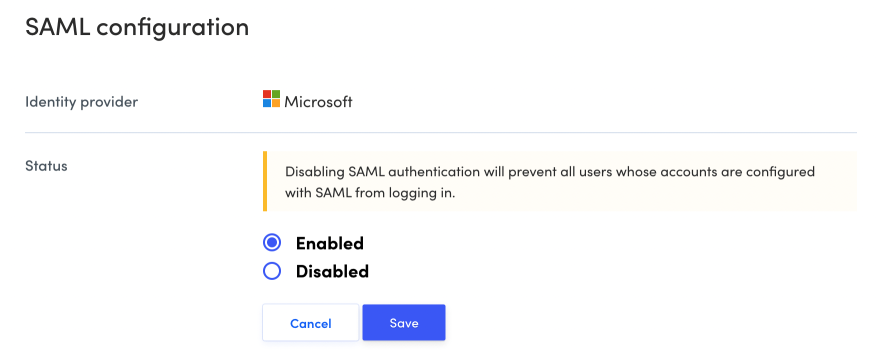
Status
This section shows the status (Enabled or Disabled) of SAML authentication.
Click Edit to change the status. Disabling SAML authentication will prevent all users whose accounts are configured with SAML from logging in.
Domain names
This section shows the domain name or names used for SAML authentication.
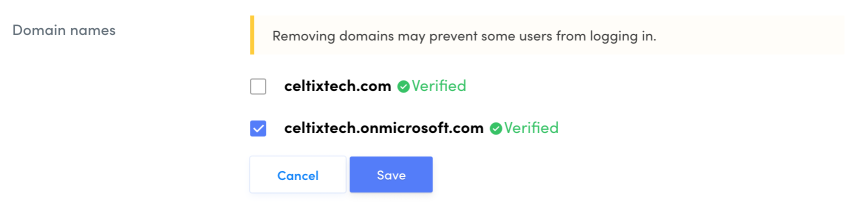
Click Edit to add or remove a domain name. A domain name must be added to the Client Portal and validated to be used (if needed, consult the procedure for registering a domain name).
Removing domain names may prevent some users from logging in.
Identity provider data
This section shows the information issued by the identity provider (Microsoft, Google, etc.).
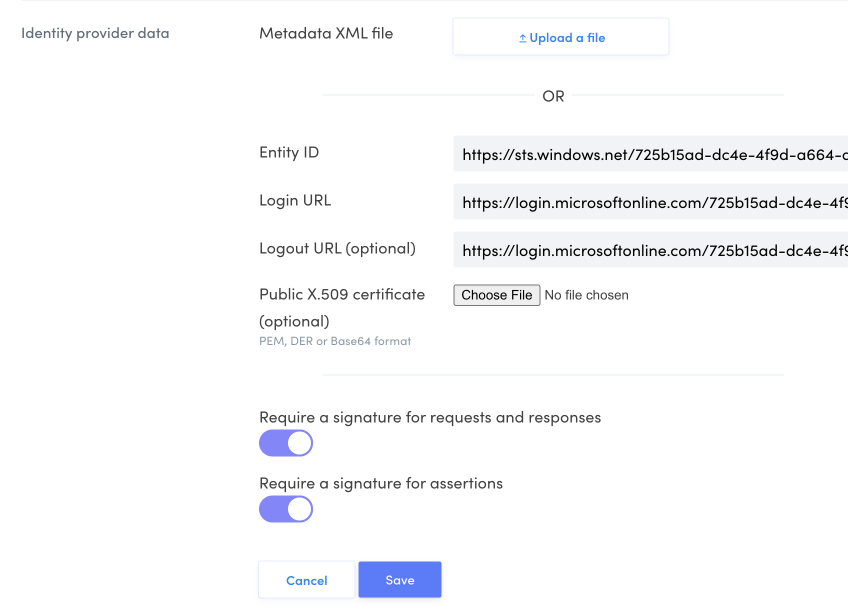
Click Edit to make changes. You can upload a XML metadata file from your provider or manually enter the data. Read the procedures for configuring SAML in Azure AD or Google Cloud to learn where this information is made available on each of these platforms.
Adjust signature verification settings depending on the identity provider.
Attributes required to configure SAML authentication with your identity provider
For SAML authentication to work, make sure the following attributes correspond to the indicated specifications. If you are using Azure AD, please refer to the section on Configuring SAML in Azure AD; if you are using Google Cloud, please refer to the section on Configuring SAML in Google Cloud.
To set up authentication with another identity provider, use following required attributes.
- Alias: emailaddress
http://schemas.xmlsoap.org/ws/2005/05/identity/claims/emailaddress
A non-null and non-empty string indicating the email address with which the user logs in to Druide’s services- Alias: givenname
http://schemas.xmlsoap.org/ws/2005/05/identity/claims/surname
A non-null and non-empty string indicating the user’s last name- Alias: surname
http://schemas.xmlsoap.org/ws/2005/05/identity/claims/givenname
A non-null and non-empty string indicating the user’s first nameName identifier format
The name identifier format expected in the response is persistent
(urn:oasis:names:tc:SAML:2.0:nameid-format:persistent).
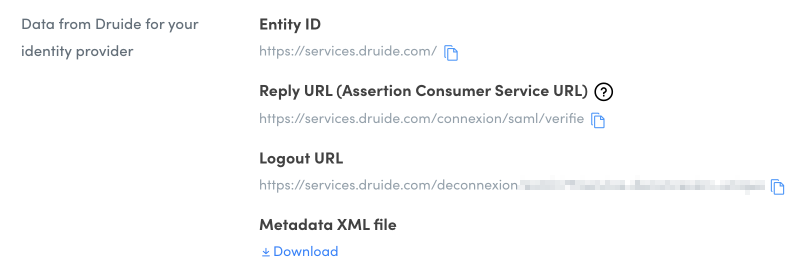
Data from Druide for your identity provider
This section shows the information you need to copy into the identity provider’s SAML configuration settings. You cannot make changes to these links; you may only copy them (by clicking the ). You can also download the XML metadata file to configure the settings automatically.
Read the procedures for configuring SAML in Azure AD or Google Cloud to learn where to enter this information on each of these platforms.
Resource person
This section shows the contact information of your organization’s resource person for matters related to SAML authentication.
Click Edit to make changes. It is recommended you assign a resource person to receive technical details in case of login or configuration issues.
Antidote Web access
If your organization has one or more active subscriptions to Antidote Web, this section shows how Antidote Web access is managed.
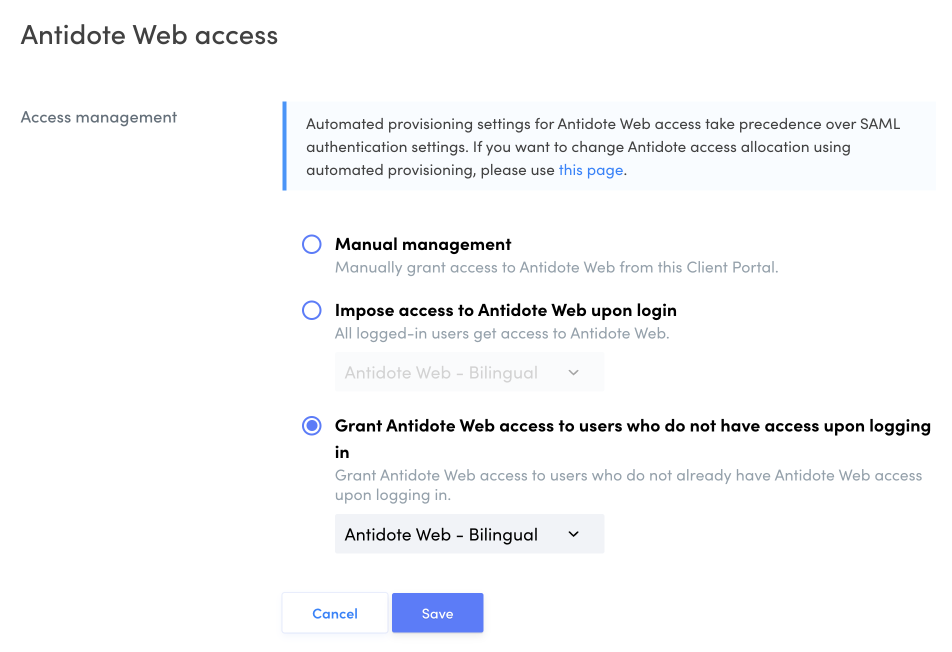
Click Edit to select one of these three options.
-
Manual managementThis option lets you grant access to Antidote Web independently of SAML authentication. You can grant users access manually from the Users tab in the Client Portal.
-
Impose access to Antidote Web upon loginThis option lets you automatically grant Antidote Web access to all users who log in with SAML authentication. If your organization has multiple subscriptions, specify which one should be used. If a user already has access to another subscription, their subscription will be changed the next time they log in.
-
Grant Antidote Web access to users who do not have access upon logging inThis option lets you grant Antidote Web access to users who don’t already have it. For example, this option is helpful if your organization already has a subscription, and you want new users to have access to a different subscription than those who already hold one.
Important — The Antidote Web access management settings configured for automated provisioning, if applicable, override the options described here. Learn more >